At Galah Cyber, we always keep our eyes open for new members of the flock. Our birds display kindness, act with integrity, and take pride in their work. We train people to be clear, consider client needs first, and foster an innate desire to help others. These are my values; ultimately, I want people who will live those values to join my business.
As an AppSec firm, we require a baseline level of technical competence. I weigh software engineering and web fundamentals highly and actively disqualify candidates who intend to follow a career in penetration testing. We provide offensive security services, but that’s not our business focus. Commercially, investing in training AppSec engineers is a twelve-month payoff period. It doesn’t make financial sense if they’re going to leave after 6-12 months because our roles do not align with their intended career pathway.
It may sound brutal, but plenty of offensive security firms want junior talent.
Most of the risks that AppSec programs try to manage will be with applications that serve content to web browsers. Of course, desktop applications, FAT clients, mobile apps, etc., exist, but we want candidates to be competent where most of the work is. Similarly, a large portion of AppSec is establishing rapport and collaborating with software engineering teams. We must help them balance engineering velocity with other non-functional requirements, including cybersecurity risk. Without experience or formal education in software engineering, logically reasoning these trade-offs without being perceived as a blunt compliance instrument becomes a challenge, invalidating any work we do.
Given that background, I want to share my learnings from a careers event that I attended to scope out good candidates.
Recently, I had the opportunity to attend the Newcastle Tech Futures event. I like to attend careers fairs to speak with students about Application Security or DevSecOps. Most students are unaware of these disciplines in Australia. Our nation needs more builders, not breakers, so I want to push more people towards engineering careers. Selfishly, I also want access to good software engineers and push them towards a career with Galah Cyber.
To help me shortlist candidates for this event, I created a quick series of challenges to gauge students’ technical ability, communication skills, and curiosity/persistence. The challenge goes as follows:
- Navigate to the challenge page. The challenge page included a decently sized CipherText with a relatively short key. The Cipher used was Vignere, and the plaintext contained the first 6-8 paragraphs of the Galah article from Wikipedia. In the middle of the plaintext, however, was a Base64 encoded string (pictured below).
- This string, if decoded, was a hyperlink to a Google form with short response questions and a link to a Galah repository where I asked them to download the codebase and write up a few pointers about issues they found and what people could do about it.

Ultimately, this challenge ticked a few boxes for me. Firstly, at Newcastle University, the Data Security course was a third-year course and covered Vignere Ciphers and how to manually break them using Kasiski or brute force. In the resulting text, they should be able to find the flag and ultimately recognise it as Base64 because of the == padding / character set. The Short Response / Code Review would then help see who is persistent, who can communicate well, and who has practical skills to interrogate and reason about security bugs in a software repository.
That was the plan.
It did not go to plan.
After distributing the QR codes, I encountered the first problem when returning to my booth. I saw about 30-40 hopeful candidates telling me they were ready for a job and had solved the challenge. I checked my Google form, which had no submissions. I was beginning to feel confused.
I asked the students to demonstrate what they did, and a few copied the plaintext into ChatGPT and asked for it to solve the Cipher, which it did. ChatGPT outed the CipherKey as Corella and then wrote the plaintext, which the students proudly presented to me.
The problem, though? The plaintext was the Galah Wikipedia article without my Base64 string in the middle. I believe the LLM saw that the first 2-3 paragraphs resembled the Wikipedia article and continued along that line without further processing.
I was surprised that nobody had worked this out by hand. But, I understood that many students today use AI to help them solve problems. I requested that the students work it out by hand to work out the next steps, and they had a go.
A few weeks later, I had a persistent student message me on LinkedIn, telling me that she couldn’t work it out and she’d put significant effort into this challenge.

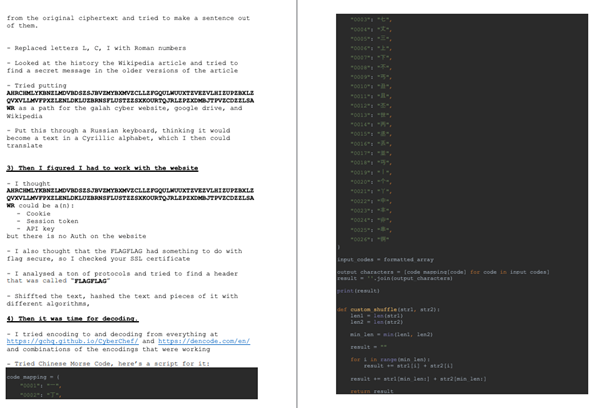
After reading through the above, I recognised that there should not be this much difficulty and that I have almost certainly made a mistake with the challenge.
I went and had a look at the CipherText and then immediately facepalmed. The terminal application I used had -k for key, -e for encrypt, but I set another flag in my haste without thinking it through. That flag was how the program handled punctuation and capitalisation. I thought capitalisation and punctuation would help with the decryption process, so I wanted to remove those.
Base64 needs both punctuation (in the form of padding at the end) and capitalisation to be functional. So, decoding the Base64 string resulted in garbage after the encryption process.
To add insult to injury, once I solved this problem, I encountered a new one.
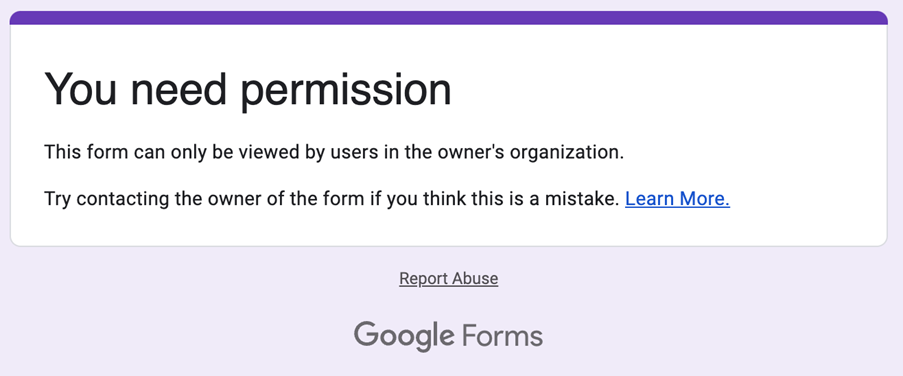
So not only did I have a broken Base64 link to my careers submission form, but even if they somehow fixed that by brute forcing through capitalisations and padding, they still couldn’t access the form because of my default security settings…
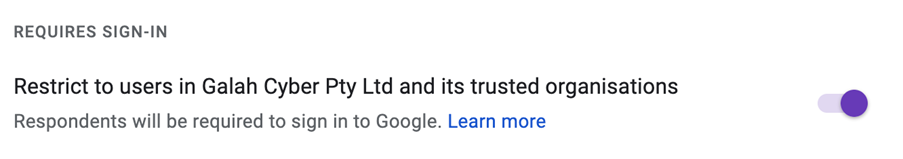
The experience has been a bit of a failure for me. I’m in the process of individually reaching out to students who contacted me and offering them a formal interview for junior positions next calendar year. But what did I learn?
- Do end-to-end testing: I went partly through this process and from my own laptop. If I tried the experience end-to-end as a student, I would have encountered and fixed each of these issues.
- Give myself more time: By only spending a short period of time to come up with this career challenge, I didn’t threat model how students would approach it with ChatGPT.
Ultimately, we want to hire good eggs, and challenges like this can backfire by also turning away potentially great candidates who may not have confidence in their ability or a different skill set than web technology. I’m privileged to have a good reputation as an employer for cybersecurity students in Newcastle, but moving forward, I will approach careers challenges differently.







